Devices that connect to a computer using Thunderbolt are given greater access than are devices that connect via USB. This is thanks to Thunderbolt’s “very privileged, low-level, direct memory access,” according to Markettos. The primary line of defence against these attacks is a system component called the Input-Output Memory Management Unit (IOMMU), but it has been found that Windows, macOS and Linux operating systems are using this component neither correctly nor efficiently. These weaknesses stretch back as far back as 2016. A number of preventative measures for malicious attacks via Thunderbolt have already been taken. For example, Apple fixed a Thunderbolt vulnerability that allowed administrator access to a system back in macOS 10.12.4.
How can I protect my computer against Thunderbolt port attacks?
In order for a hacker to target your computer via Thunderbolt they must have physical access to your machine, then plug in some form of external hardware that might contain malicious software. All computers with Thunderbolt ports are vulnerable to such threats since the port itself is not to blame, rather the method of data transfer used by Thunderbolt. You can tell if your PC or laptop has a Thunderbolt port by checking its documentation, specifically where it lists the number- and type of ports offered. Thunderbolt uses a MiniDisplay- or USB-C port, which are illustrated below.
The majority of Thunderbolt vulnerabilities have been fixed through software updates from operating system manufacturers issued in the past few years, but devices that shipped before the release of Windows 10 1803 will be vulnerable due to a lack of firmware support. The best way to ensure no-one is able to attack your computer via its Thunderbolt ports is to ensure you:
Never leave your laptop in an area where it can be easily accessed by other peopleIf you’re not sure where a peripheral has come from or who has had access to it, don’t plug it into your device
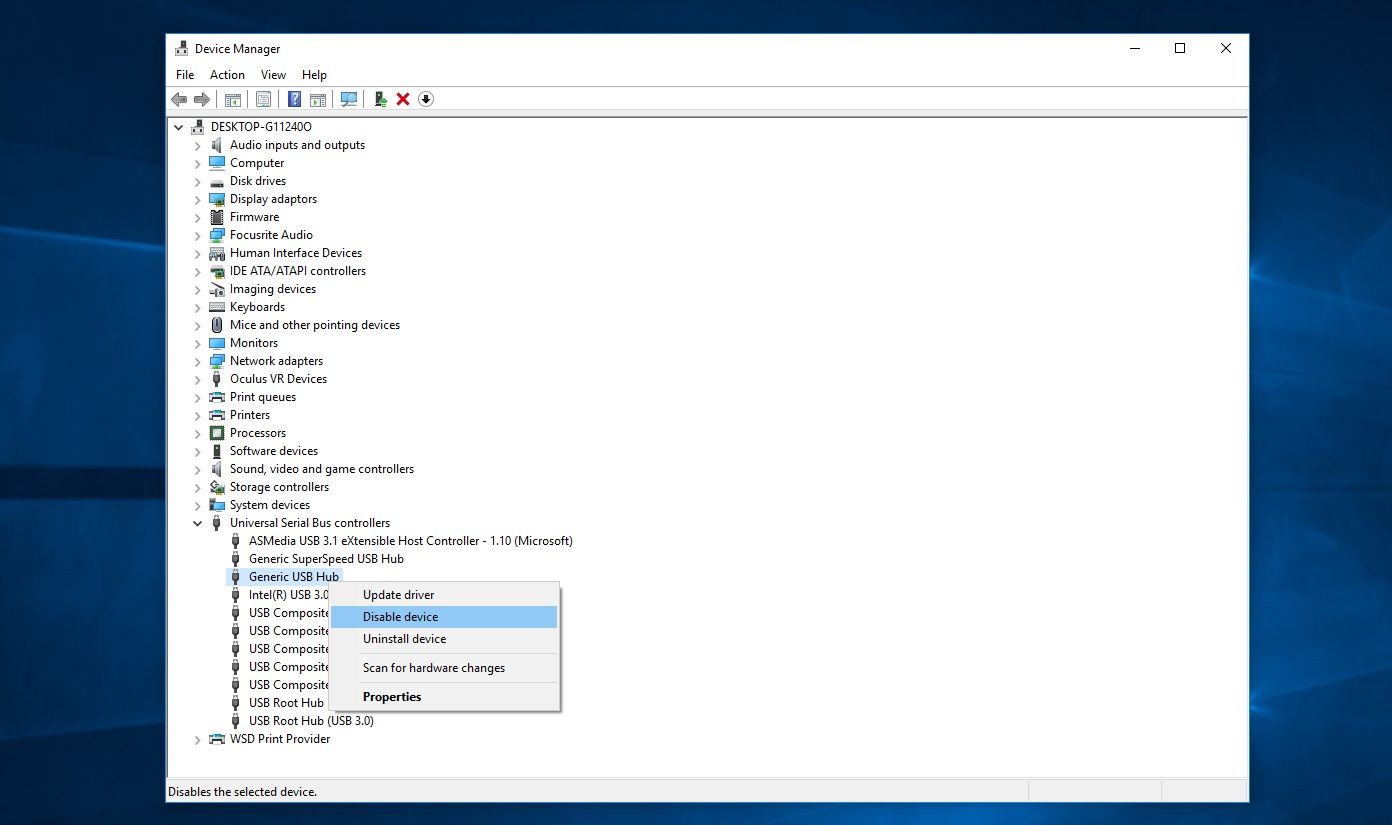
Any peripheral could contain malicious software. Storage devices, external GPUs and even chargers can be infected with malware if someone has taken the time to install the program on to the device. A good way to ensure you’re getting peripherals that are clear of malware is to purchase them from reputable suppliers only, avoiding secondhand- and cheaper third-party alternatives. Thunderbolt ports are often combined with USB-C ports in an effort to help save space, so an extreme way to protect them is to temporarily disable your computer’s USB ports when you aren’t there to keep an eye on it:
Search for and select ‘Device Manager’ at the bottom left of WindowsScroll down to and select ‘Universal Serial Bus controllers’Any currently unused USB ports will be displayed as ‘Generic USB Hub’Right-click any port and select DisableTo later re-enable your USB ports follow the above process but select Enable rather than Disable
What to do if you think you have malicious software on your computer
Everyone should have an antivirus on their computer, so take a look at our Antivirus deals article to make sure you’re getting top-notch protection at the best price. We recommend Bitdefender or Norton.
A VPN can help keep your location and identity safe on the internet (if you don’t know what a VPN is, we have an explainer here) and we’ve got a list of our favourite VPN services right here. Our top pick is NordVPN.
We also have an article on the best ways to protect yourself online, what to do if you think your PC has been infected with a virus and, should the worst happen, how to remove a virus from windows if you’ve lost control of your PC.
Related articles for further reading
All security news Best antivirus software for Windows (plus free options) Best antivirus deals Best VPN services (plus free options) Best VPN deals